Hacking Tool
Knock – Open Source Subdomain Scanner Tool
Knock – Open Source Subdomain Scanner Tool
Knock is a python based tool for enumerating subdomains on a targeted domain. You can use a custom wordlist and also you can scan a domain for DNS zone transfers. It also supports queries to Virus Total subdomains.
Installing Knock
First things first, you have to install the dependencies manually.
apt-get install python-dnspython
After that clone the Github repository to your machine. Then, follow the instructions below.
git clone https://github.com/guelfoweb/knock.git cd knock/ python setup.py install
Running Knock
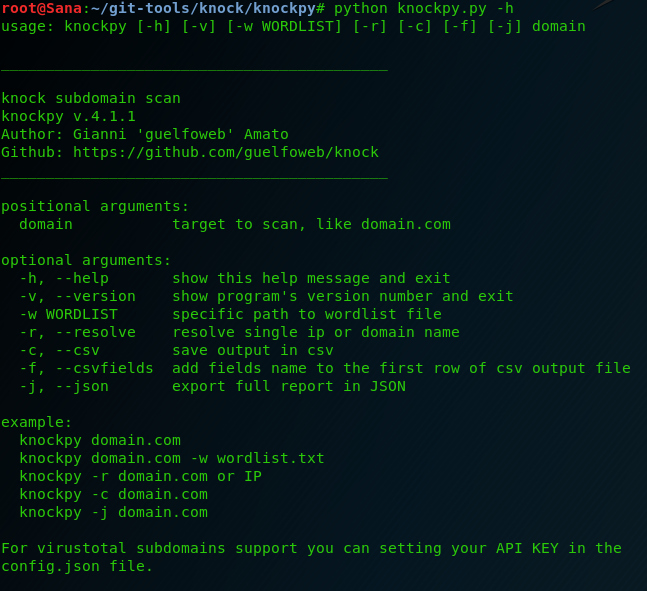
Let’s first see all the available commands.
cd knock/knockpy/ python knockpy.py -h

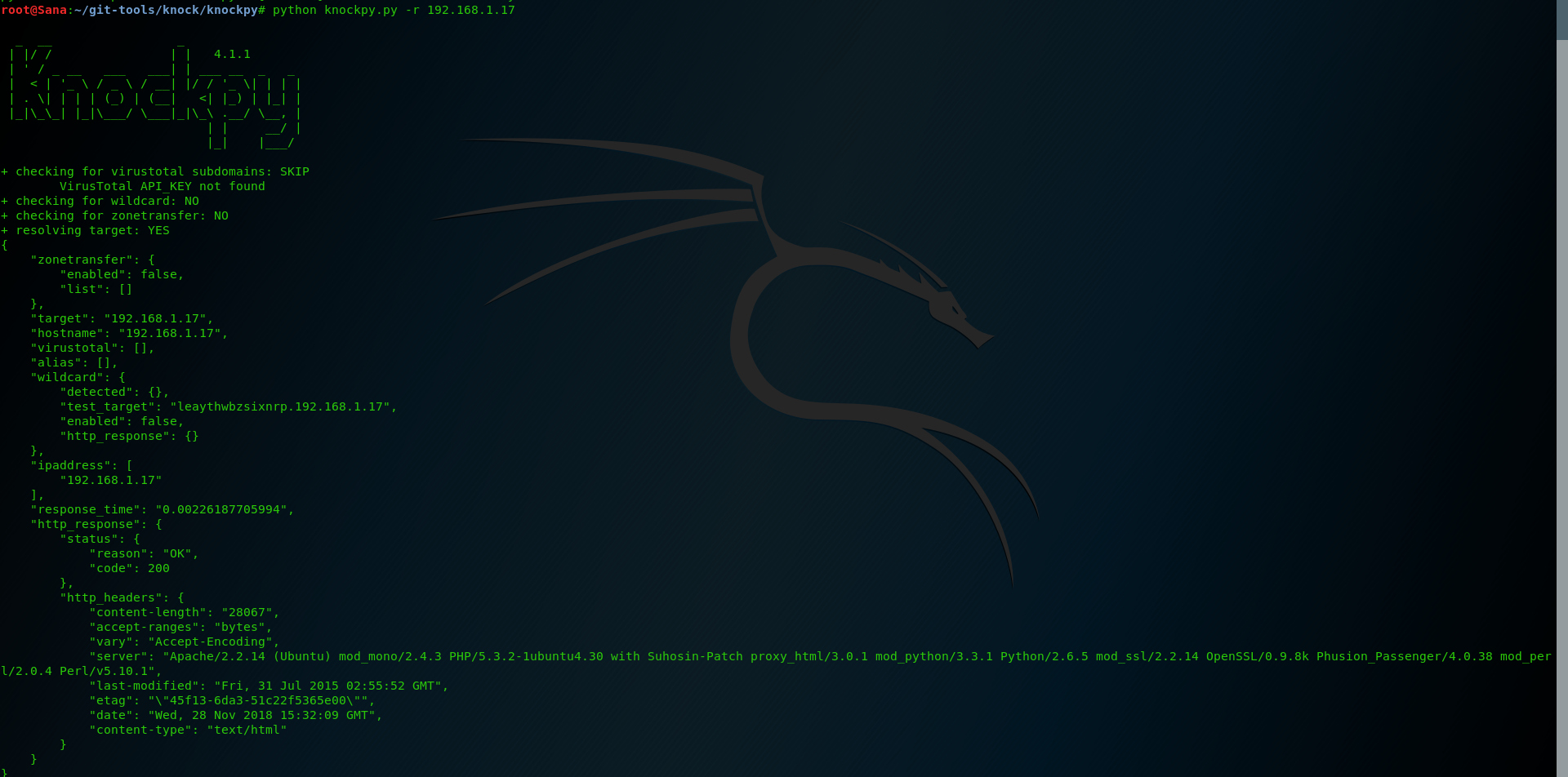
Very simple interface, you just have to type the domain you want to test. If you want, you can use your own custom word list. Also, it gives you the option to export your results in JSON or CSV format. In the example we typed ‘python knock.py -r (site)‘ and we got some basic info about the DNS transfer zones and wildcards. It’s very useful to have this info to perform exploitation later.
You can also go to THIS address, to add the Virus-Total API in the knock.py script.

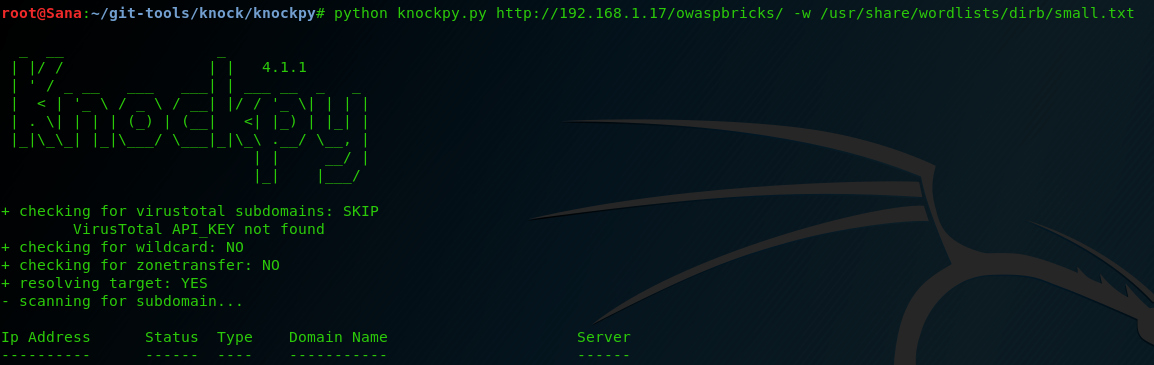
Let’s now use a custom wordlist to check for subdomains. Use the command below to test it. The scan may take several minutes to complete.
python knockpy.py (domain) -w /usr/share/wordlists/dirb/small.txt
In my example, the host doesn’t have any subdomains. However, in a real host the results will be shown in the table below.

What Bunny rating does it get?
Knock is very smooth for subdomain enumeration. However, I think it is a bit slow in comparison with other tools I have tested. So, I’m giving it 3 out of 5 bunnies.
👽👽👽👽👽👽👽👽👽👽👽👽👽
Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.



Post a Comment
0 Comments